"There's been an enormous amount of insecurity around the world. I think 2026 is gonna be a busy year in terms of cyber attacks."
These words echo the exponential growth in cyber attacks since the start of the pandemic. And with the introduction of hybrid and remote work, hacking has never been easier.
With so many possible targets, both corporate and individual, it’s hard to keep an eye out for everything. As a result, the demand for cyber security specialists is on the rise.
Among these experts, penetration testers stand out with the most versatile skill set.
Why?
Because their work is not limited to sitting behind a desk.
Sometimes they must go to where the work is. And infiltrate the target’s physical space before proceeding with its systems.
But how do you get one foot in the door of this industry?
With a great resume, of course!
Whether you’re playing for the blue or the red team, you must prove you’ve got what it takes to be a pen tester.
How?
This article contains all the tips you need to know to start your pen tester career in 2026.
The examples in our complete guide will teach you
- What do recruiters consider the perfect pen tester candidate
- How to choose the best resume format so you can highlight your strengths
- How to make the most of your resume summary
- Which skills are trending for penetration testers
- Whether formal education is mandatory and which ones are preferable
- Which are the top certificates for cyber security specialists
- How to prepare and plan ahead for the interview
Looking for related resumes?
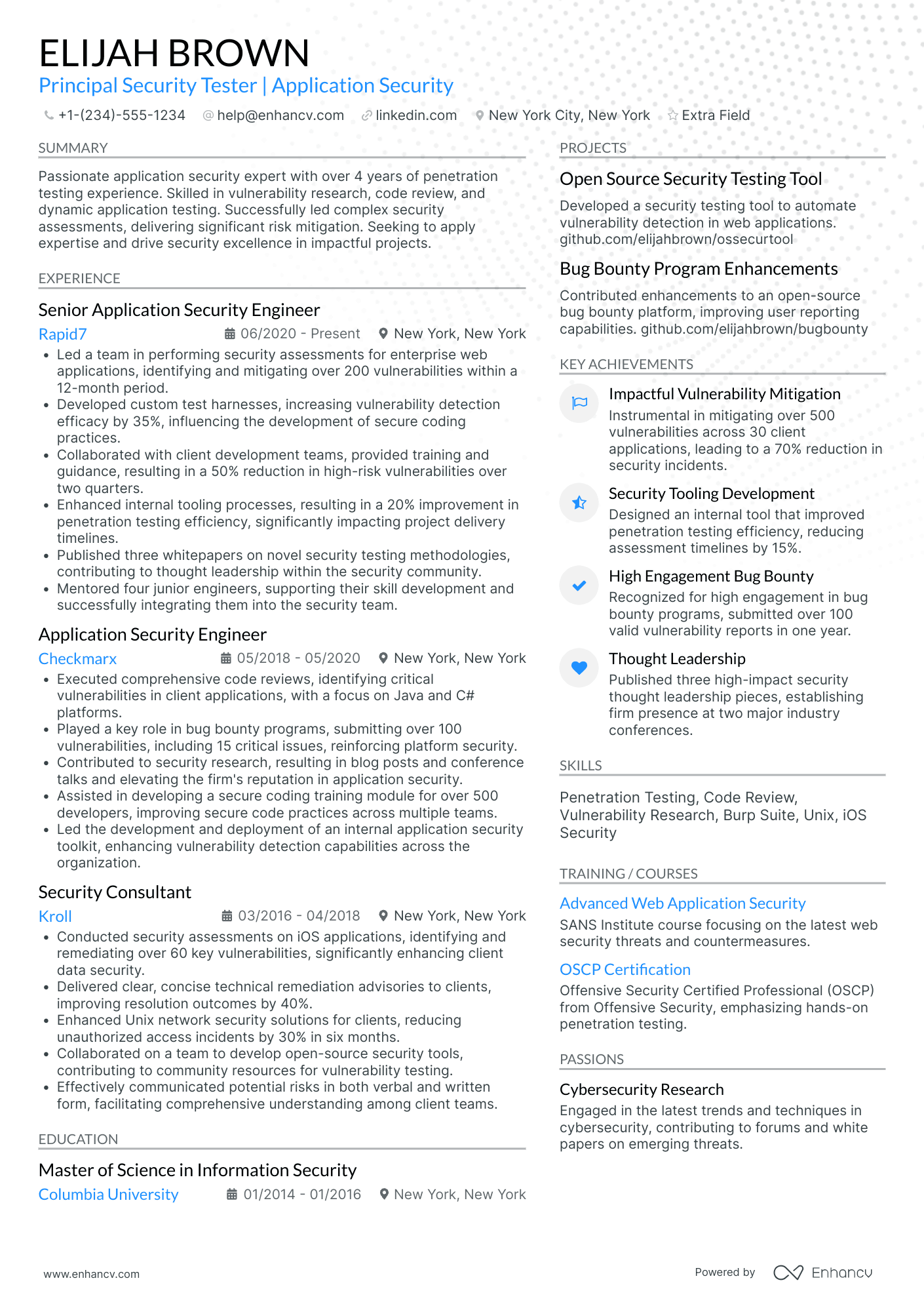
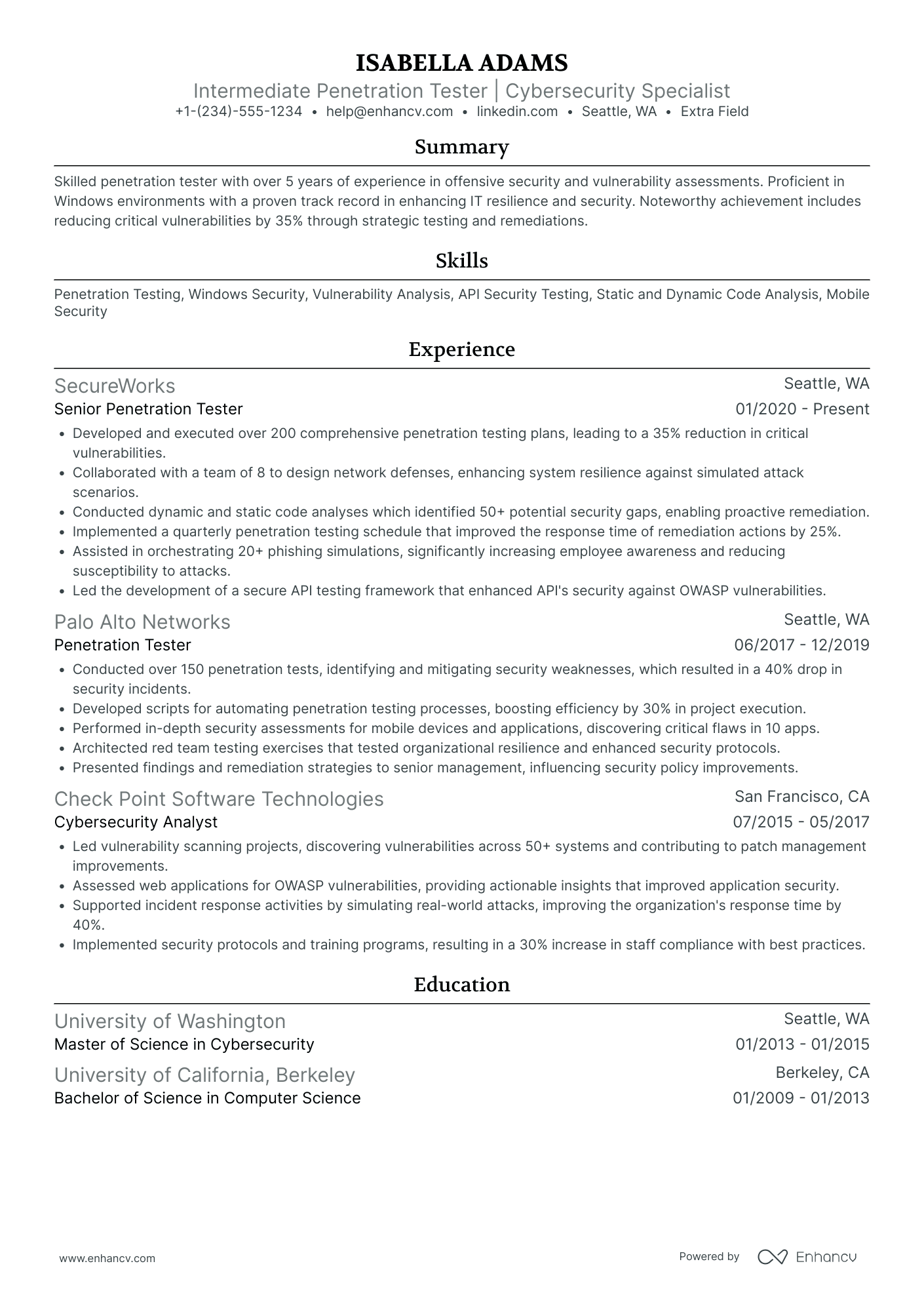
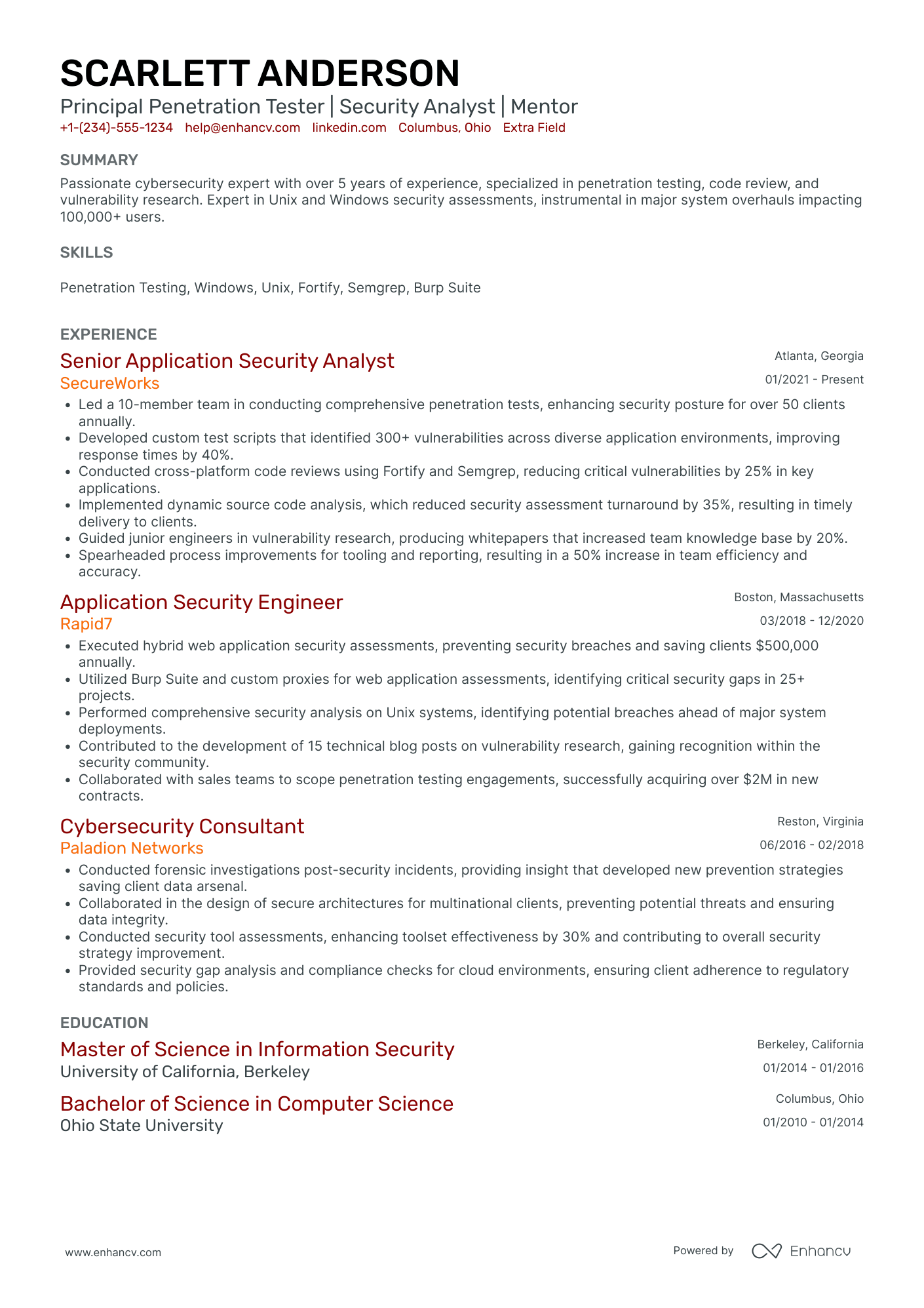
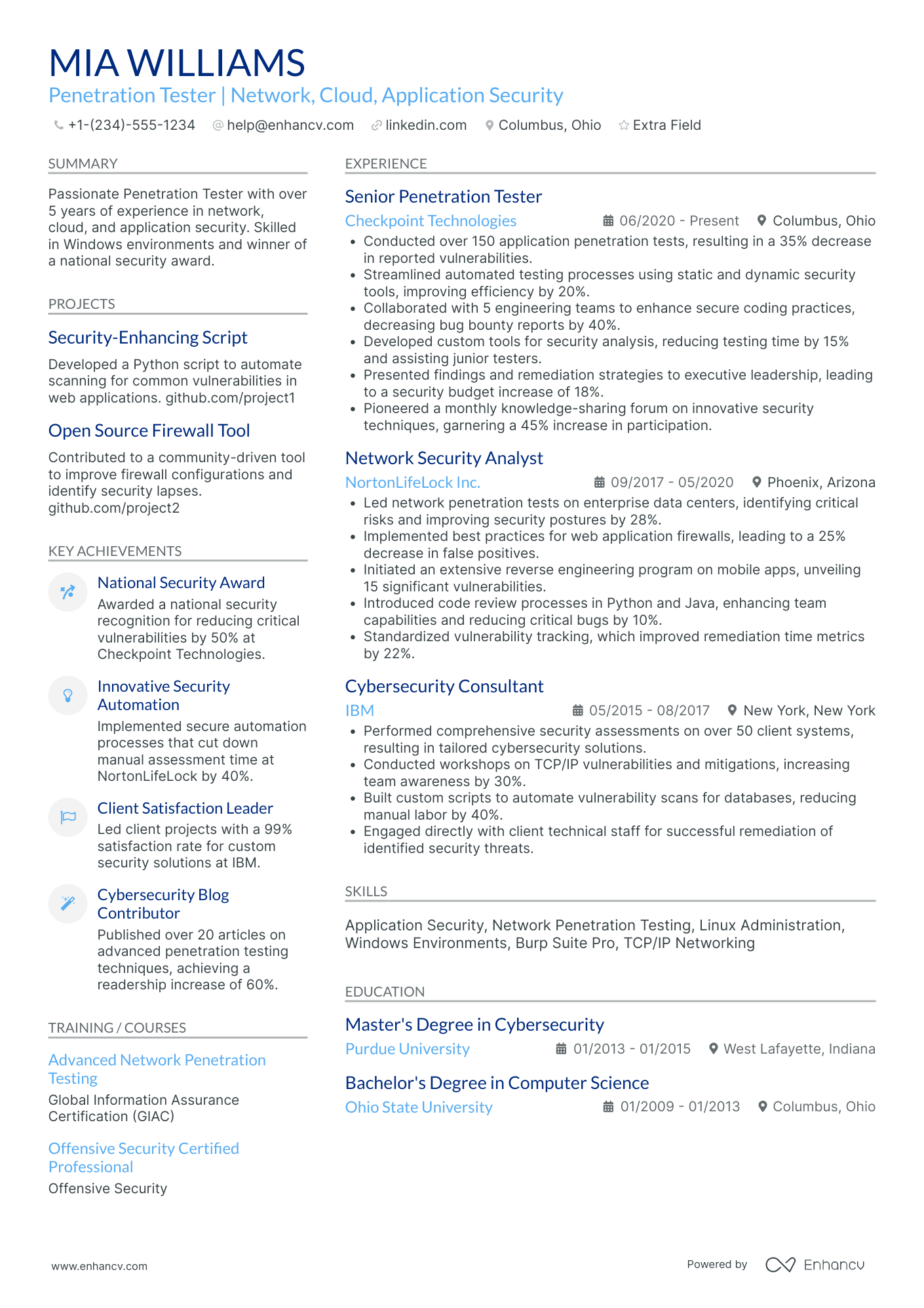
Penetration tester resume: how to secure an interview with recruiters
There are so many ways to get into the cyber security industry!
But you’ll have to be prepared to do the work. Especially if you’ve decided to switch careers from a non-tech field.
Can you still apply to become a pen tester, if you don’t have a tech background?
Yes!
Some of the currently active pen testers started out as military personnel. Others as law enforcement members.
And there are those who have made the 180 degree shift. From convicts to cyber security specialists.
Wait, what do vets, the police and prisoners have in common? As Bryan Mills, played by Liam Neeson, once said: a very particular set of skills.
But that’s not all. They also share:
- Drive to learn
- Curiosity
- Willingness to use their skills for good
- Creativity
- Resourcefulness
- A can-do attitude
- Efficiency
As well as many other relevant personal traits.
That’s why it’s important to show you character. And describe the scope of your current abilities, including transferable skills.
You never really know which will come in handy on the job.
And the sooner you do it, the better.
We’ll review each resume section individually later. For now, let’s look at the resume in general.
What do you need to keep in mind when building yours?
The type of skills and the amount of experience you have will determine the format of your resume.
If you’re a recent college grad, it’s best to use the functional resume.
Its layout will allow you to start with your most relevant skills. And any academic projects or side gigs to support your claims.
Then you’ll add your formal education, making sure to mention related majors and courses.
You’re switching careers? Before you choose a resume format, you need to assess your experience. And the amount of overlap between your work history and cyber security.
If your past experience isn’t related, the functional resume is still your best option. Highlight your transferable skills and tie them to the job description.
But remember, you must display some relevant experience. Even if it doesn’t fit into the past work history category.
Links to completed courses, VDP reports or bug bounties earned boost chances. You must also feel comfortable being tested on the tools you’ve listed on your resume.
Yet, if your work is closely tied to the high-tech industry, then use the hybrid resume.
This layout will help you present the overlap in work experience. And any transferable skills you have to offer.
Finally, if you’re a tenured professional, stick to the traditional reverse-chronological resume. The key is to shine the spotlight on your proudest achievements.
Be succinct and to the point.
This is what a rough sketch of your resume should look like:
Key resume sections to have on your penetration tester resume
- A header to link to your professional profiles and portfolio
- A resume objective or a summary to draw attention to your accomplishments
- An experience section to share the wide range of your expertise
- A skills segment to exhibit your versatile skill set
- An education and certificates box to emphasize your qualifications
- Extra sections to feature additional relevant information
Very simple and straightforward!
With this in mind, now it’s time to focus on what you should include on your resume. You must frame your experience in way that will both:
- Appeal to your potential employer’s mission and current goals
- Impress hiring managers with your abilities
Here are some questions to consider when writing:
What do recruiters focus on when reviewing resumes?
- What made you consider a career in penetration testing?
- Why make the change now?
- Do you have any related personal projects? Which one is your favorite one and why?
- What is penetration testing to you?
- Can you provide a definition of pentesting?
- What are the main goals when conducting a penetration test?
- What is OWASP Top Ten? Can you list them all?
- Are you familiar with any other pentesting methodologies?
- Do you know how many penetration testing phases there are? Describe them.
- What is the primary difference between symmetric and asymmetric cryptography? Can you give examples?
- Do you know the OSI model layers? Can you name each layer and give examples?
- Which are your favorite exploit tools? Provide examples on exactly how you’ve used them.
- Do you have any certifications?
- Which is your favorite pentesting technique? Why?
- Which team do you have most experience with - blue, red or purple? Which one is your favorite? Would you consider switching?
Many of the questions above may be asked during your interview. So keep track of what you include and refrain from lying or exaggerating on your resume.
Being new to an industry may be scary. But it’s never a good idea to mislead hiring managers.
Impressing recruiters with your penetration tester resume header
Although short this section has a great impact on your resume's performance. Hiring managers spend 6 to 7 seconds on average looking at a resume.
And you need to catch their eye for all the right reasons.
How do you do that?
Think of the resume header as your business card. Or a professional social profile. Add only your most basic information:
- You first and last name
- Your address (city and state is enough)
- Email and phone number
- Job title (or the name of the position you would like to fill)
- Links to your portfolio
- Links to your professional profiles (Bug Crowd, HackerOne, Intigriti, GitHub, etc.)
To see how messing up with your resume header can affect your chances, compare the samples below.
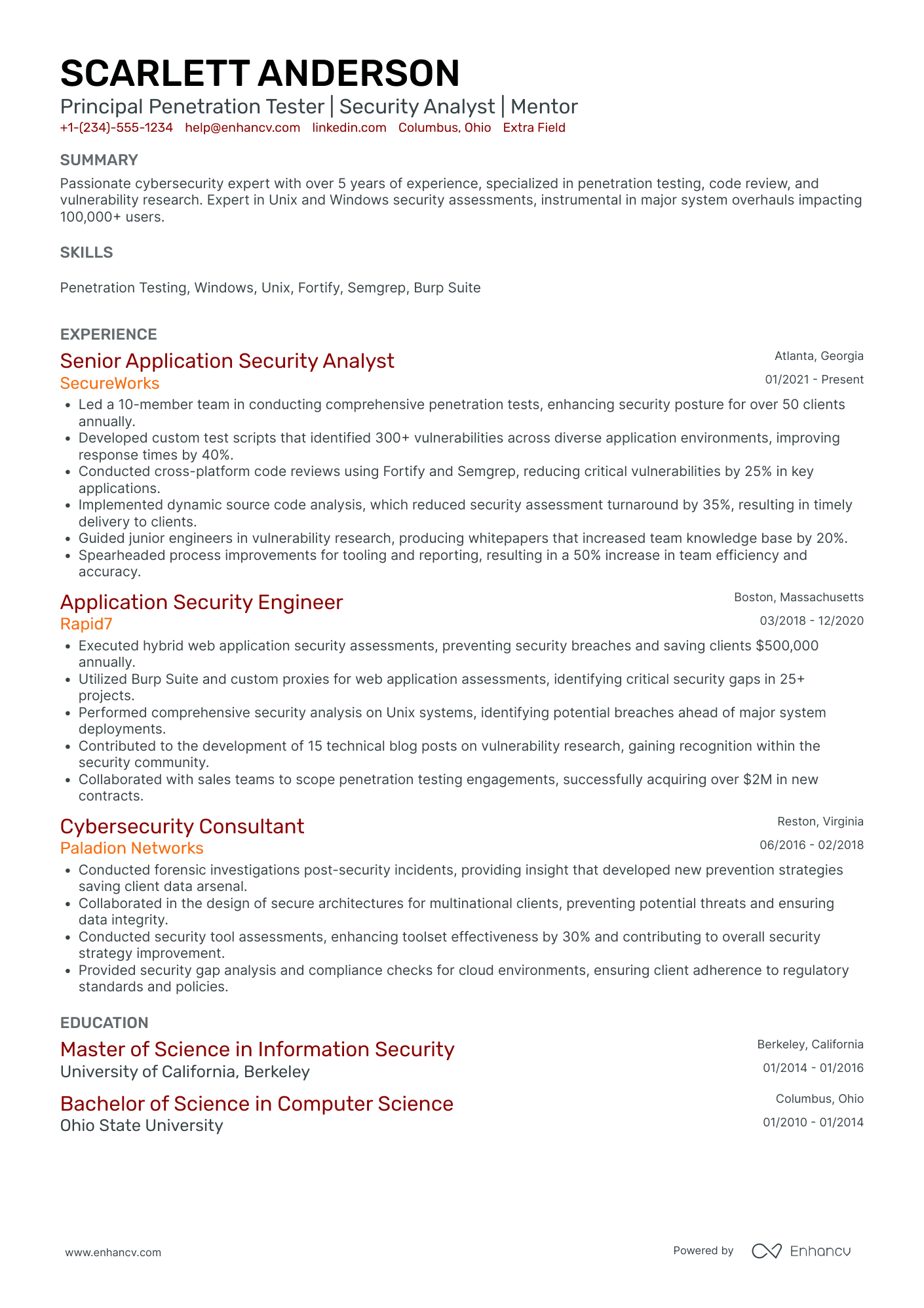
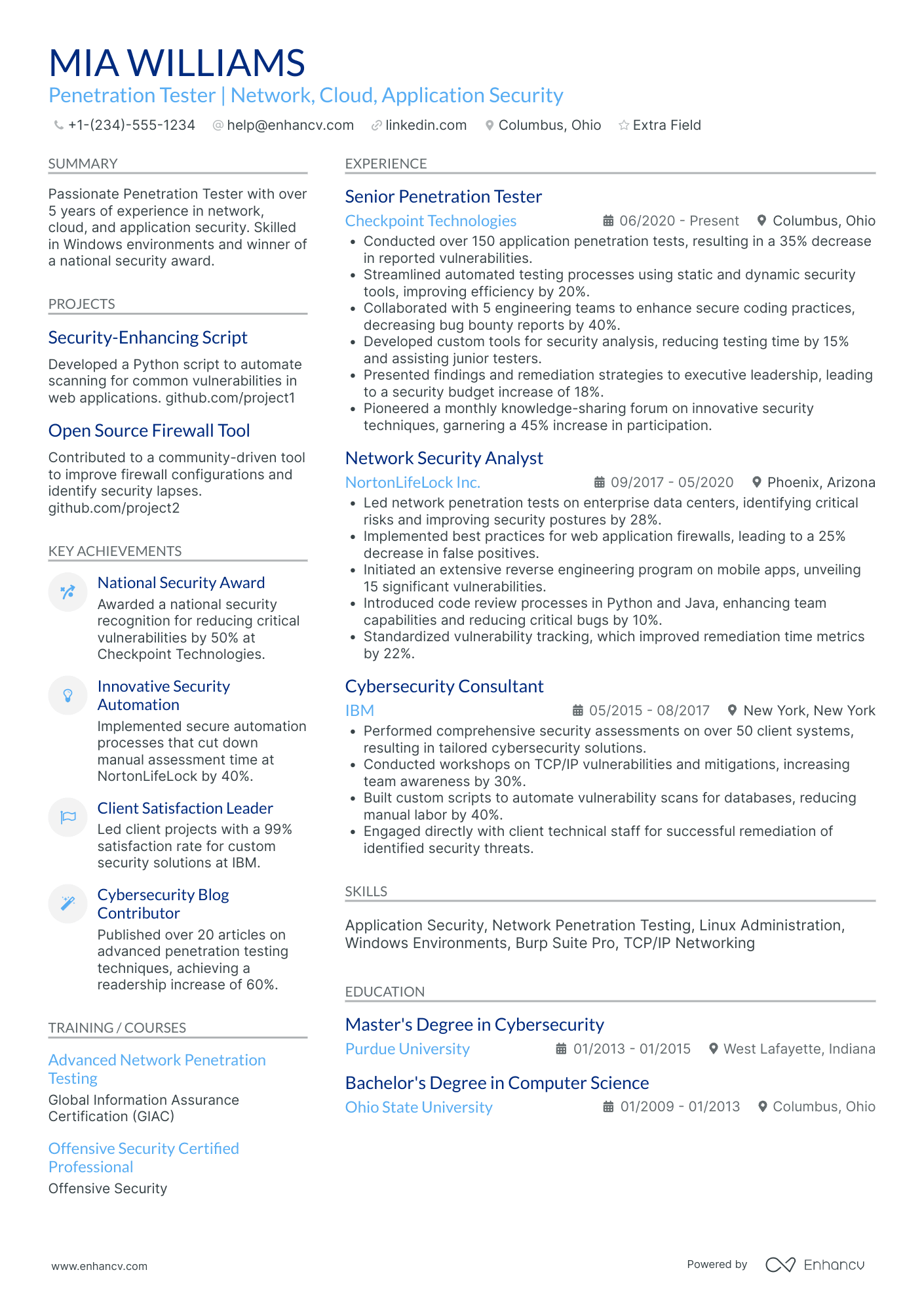
2 penetration tester resume header examples
What are the issues here? Well, three stand out the most:
- Jamal’s job title is misleading. He could be referring to working as a security guard. Or an individual providing cyber security services.
- The phone number is missing. Some hiring managers prefer to conduct a short phone interview when vetting candidates.
- There are no links to either a portfolio, or an account on any related professional platform.
The last point is very important. Recruiters like to see applicants who are passionate about what they do.
You have to show you’re actively involved in pentesting by linking to side projects and bug bounties.
Just make sure to fix any typos and misspelled words. Check for broken links before you continue with the next section, too.
Summarizing your best achievements for your pen tester resume
The best way to follow up a good resume header is with an excellent resume summary.
Keep in mind the 7 seconds rule we discussed. Having listed your basic info, you now have 4 seconds left to grab recruiters’ attention.
Engage them by highlighting your proudest pentesting moments. Share honorable successes and list the skills you’ve used to achieve them.
But what if you’re at the beginning of your career? Then you should write a resume objective.
What’s the difference?
More experienced professionals write summaries to give a sneak peek into their expertise. Instead, college grads and those changing careers should write a resume objective.
Like the summary, its purpose is to feature relevant skills and experience. But it’s also a way to show potential employers how you would use your abilities to their benefit.
2 penetration tester resume summary examples
Have a look at the sample resume objective below:
How many mistakes do you spot here? Let’s look at a few.
There’s no mention of either the name of the completed course, nor the education provider.
And with the quality of this resume objective, recruiters won’t stay long enough to read the rest. Which means, they won’t be able to verify any credentials. Even if they are listed.
What’s more, the potential employer’s company name is misspelled. Here is where attention to detail is crucial.
Not only is this unprofessional, but it also shows the candidate doesn’t pay attention to details.
And speaking of abilities, the applicant has listed two technical skills. But no proof to support the claims.
How can this resume objective be improved? Check out the following example below:
This is much better!
Yes, the candidate is a beginner pen tester. Yet, the passion and enthusiasm is evident.
What’s more, the applicant has some experience. They show that cyber security is more than just a hobby. It’s a thought out career choice.
The best part of this resume objective is that the candidate has planned their career growth.
They have a specific field of interest. And the applicant is actively pursuing extra training to develop their skills.
Optimize your resume summary and objective for ATS
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
How to let your resume experience section do all the talking
We’ve come to the most dreaded part - the experience section. But worry not, it’s not as difficult as you think.
All you need to bear in mind is how you frame your work experience.
Concentrate on what your potential employer will consider benefits. Appeal to their mission, goals and future plans.
If you know they need a red team member, highlight your offensive pentesting skills.
Remember, your resume will be looked at by both HR and senior penetration testers. So your experience entries must be concise and understandable.
After all, one of the most popular abilities for pentesters is presentation skills. You must be able to explain what you do and how you work.
But how?
Lead your entries with results. Display the impact of your work and provide context.
2 penetration tester resume experience examples
Take a look at the sample below:
- •Earned more than $3 million in revenue for 2021.
- •Won 12 DoD cybersecurity contracts.
- •Mentored staff on identifying and properly handling suspicious emails.
There are some glaring issues here.
First, while Jamal is being succinct as he should, some key details are missing. The company description is short and, well, not very descriptive.
Also, there is no link to a company website.
More crucial than all of the above are the experience entries. Jamal has shared some notable achievements, yet they lack the proper context.
For example, he states that he has mentored staff to identify email scams. But what was the result? Did his students actually learn anything?
Finally, Jamal isn’t paying attention to the finer details. It isn’t clear whether the date on the experience entry is the start day. Or if the job is still ongoing.
Here is how a few edits can change the whole feel of the entry:
- •Earned more than $3 million in revenue for 2021, following the successful completion of over 50 penetration tests.
- •Won 12 DoD cybersecurity contracts, after successfully presenting on various case studies at Def Con in 2019 and 2020.
- •Decreased phishing attack reports by 75% for 8 clients as a result of mentoring staff on identifying and properly handling suspicious emails.
Impressive, right?
Let’s move on to the talent section.
Which are the must-have skills for your penetration tester resume?
The list is long. There are just so many of them. Which ones you choose will depend on the job description and the position you’re aiming for.
That’s why it’s more important how you describe them.
Going back to the experience section. The method is similar:
- Explain the challenge
- Lead with data
- Provide context
This method is also known as C-A-R. The acronym stands for Challenge-Action-Result.
Don’t forget to emphasize the role of your talents in your entries.
If you have extra things to brag about, this is your chance. Treat the skills section as an extended experience section.
How to highlight technical abilities on your resume
We know you know your tools. But as a penetration tester, you must be able to explain your work to non-tech individuals.
Technical managers want to see the methodologies you use. And how diligent you are when at work.
Are you familiar with the best use of your tools? Do you know at which stage of the pentest to apply them?
If you struggle to untangle your hard skill set, try to review past projects:
- Describe the case
- Write down the different tools that were at your disposal
- Include a short description of how they were used
If you need some inspiration, check out our suggestions in the table below:
Panel: Top technical skills for penetration tester specialists |
Top technical skills for penetration tester specialists
- Nmap
- Kali Linux
- BackTrack
- SamuraiWTF
- Parrot
- Metasploit
- Kismet
- THC Hydra
- soapUI
- AppScan
- ZAP
- SOOS
- Canvas
- QualysGuard
- ArcSight
- Splunk
- Archer
- Nessus
- Nmap
- Nikto
- Wireshark
- WebInspect
- Netsparker
- Fortify
- Ounce Labs
- Acunetix
- SQLmap
- SAST
- DAST
- Social-Engineer Toolkit
- Objective-C
- Java
- C#
- C
- C++
- Python
- SQL
- ASP.NET
- PHP
- JavaScript
- Bash
- Ruby
- REST
- Powershell
- XML
- YAML
- JSON
- Protocols: FTP/POP3/IMAP/SMB/SSH
- TCP/IP
- Windows/iOS/Android/Linux/Unix
- Firewalls
- Networks
- Servers
- Cloud Infrastructures
- CI/CD
- Keyloggers
- Cryptography
- IDS
- IPS
- Technical writing
- Hardware
- OSI layer model
How to leverage the social talents section on your resume
By contrast, hiring managers want to see good presentation abilities. Among other soft skills, such as creating well-structured and understandable texts.
Will you be able to write technical documents? How about negotiating contracts with business owners? Or coaching non-tech individuals?
These are crucial in the cyber security field. After all, humans still remain the weakest link in any security infrastructure.
Hence, you must demonstrate you know how:
- Individuals would act in various scenarios
- To exploit the human element if the job requires it
- To identify possible security breaches and mentor others on how to mitigate the risk
Just remember, always tie your skills to verifiable results.
Have a look at the following examples:
Wow, excellent entries which will definitely draw recruiters’ attention!
The last one is particularly impressive.
Why?
Because while the applicant describes their resourcefulness, they share so much more.
The candidate also shows creativity, leadership and teamwork skills. All in the middle of a penetration test operation no less.
Again, think of your past projects. Share how your soft skills have affected your work. And the people you work with.
Here are some of the trendiest social talents for cyber security professionals:
Important social abilities for penetration tester experts
- Ambitious
- Self-starter
- Analytical skills
- Problem-solving skills
- Decision maker
- Strategic thinking
- Explorer
- Passionate
- Ability to work individually
- Team player
- Agile
- Flexibility
- Quick
- Efficient
- Willingness to learn new things
- Patient
- Attention to detail
- Results-oriented
- Multitasking
- Inquisitive
- Open-minded
- Inquisitive
- Time management skills
- Mentoring and coaching skills
- Presentation skills
- Ability to work under pressure
- Dynamic
- Resourceful
- Creative
- Thoughtful
- Trustworthy
- Responsible
- Accountable
- Communication skills
- Risk and compliance regulations
- Risk prevention
- Vulnerability management
- Incident management
- Conflict resolution
- Negotiation skills
- People management
- Ability to build relationships
- Leadership skills
- Psychology
- Social engineering
- Personable
- Persuasion skills
Is formal education mandatory for a pen tester professional?
Yes and no.
Many companies do demand an academic background from their candidates. And some of the most common degrees are:
- BA or BS in Computer Science
- BA or BS in Information Security
- BA or BS in Information Technology
- BS or MS in Computer Engineering
- BS or MS in Network Engineering and Security
- BS or MS in Computer Forensics
- BS or MS in Cybersecurity
Despite what's in the job descriptions, you can apply without a diploma. The catch is, you must have practical experience and certificates.
Which certificates will grab recruiters’ attention?
Speaking of certificates, in some cases these are better than any diploma.
Why?
Managers of penetration tester teams prefer experience to education. Most college degrees stay within the realm of theory.
Instead, pentester courses are often built on the basis of practical exercises.
We’ve gathered a list with the trendiest certificates for 2026.
Vital penetration tester certificates for your resume
- DoD 8570.01-m
- CCNA (Cisco Certified Network Associate)
- CWNA (Certified Wireless Network Administrator)
- CompTIA Network+
- CompTIA Security+
- CREST certifications
- IBM certifications
- AWS Security Certificate
- AWS Advanced Networking Certificate
- Offensive Security Certified Professional (OSCP) certification
- PNPT (Practical Network penetration tester),
- EJPT (eLearnSecurity Junior penetration tester)
- CISSP (Certified Information Systems Security Professional)
- CEPT (Certified Expert penetration tester)
- CPT (Certified penetration tester)
- LPT (LIcensed penetration tester)
- ECSA (EC-Council Certified Security Analyst ECSA)
- CEH (Certified Ethical Hacker)
Are there any other sections which can boost your chances?
Of course, especially if you’re switching careers or a college grad.
You may not have the work history, but any participation in:
- CTFs
- Hackathons
- Ethical hacking or computer clubs
- Membership Associations
- Documentation and patents
- Bug bounties, VDPs and Zero days
- Side projects
- PentesterLab badges
- HackTheBox completed boxes
- HackerOne, Intigriti or Bug Crowd badges and rankings..
…are brag-worthy items to add on your resume.
Just look at the variety of opportunities you have to stand out!
Key takeaways: hacking your way to your dream job
- Carefully read the job description and tailor your resume accordingly
- Treat the resume header as a business card. Don’t forget to link your hacker profiles.
- Make your resume summary concise and to the point. Highlight your best achievements.
- Provide results and context for each entry in your experience section.
- Make a skills list and describe how you have applied each skill by referring to a specific situation.
- Mention relevant college majors in the education section if you’re a college grad
- Add related certificates and bug bounty achievements to get noticed by recruiters
Penetration Tester resume examples
By Experience
By Role