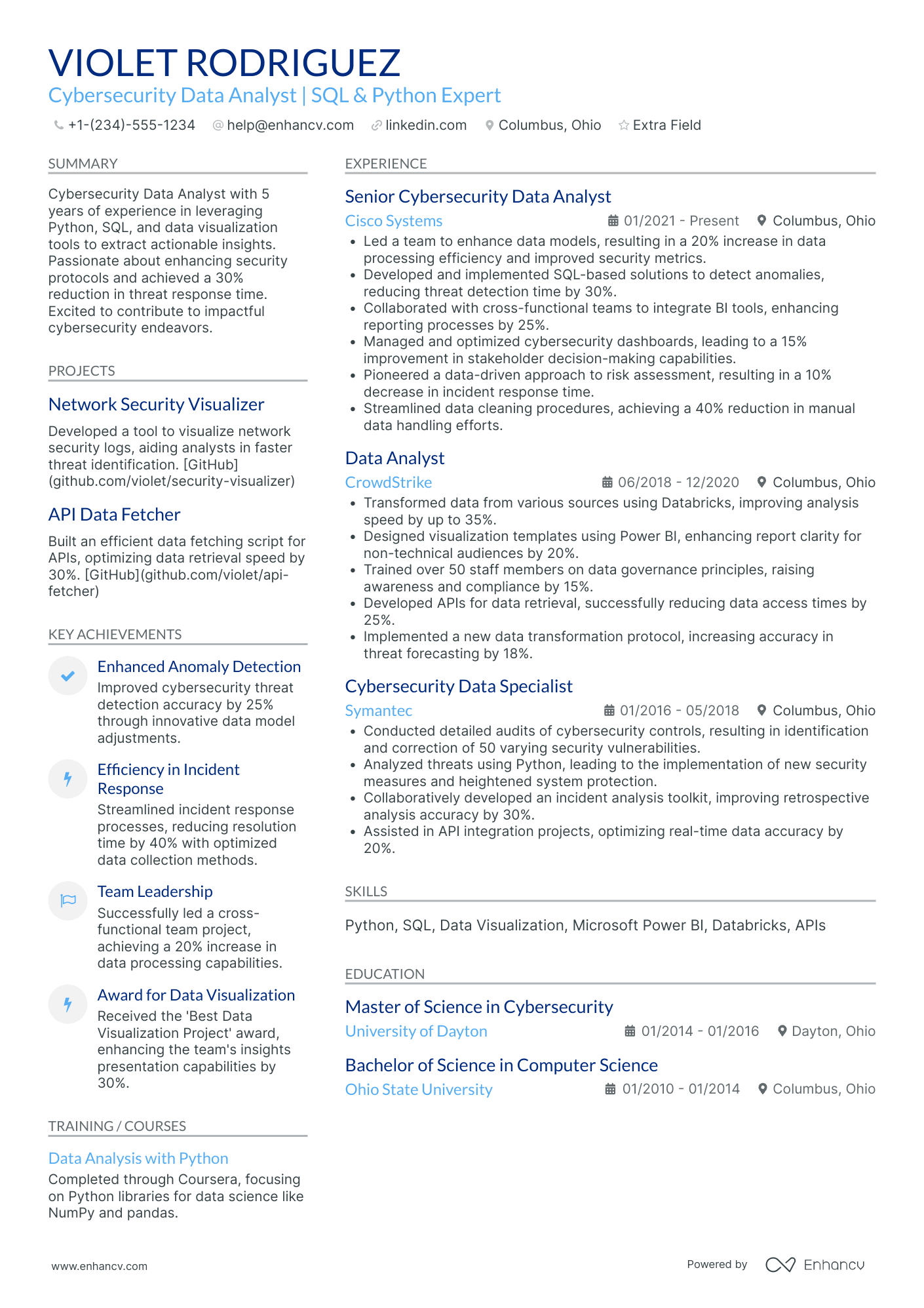
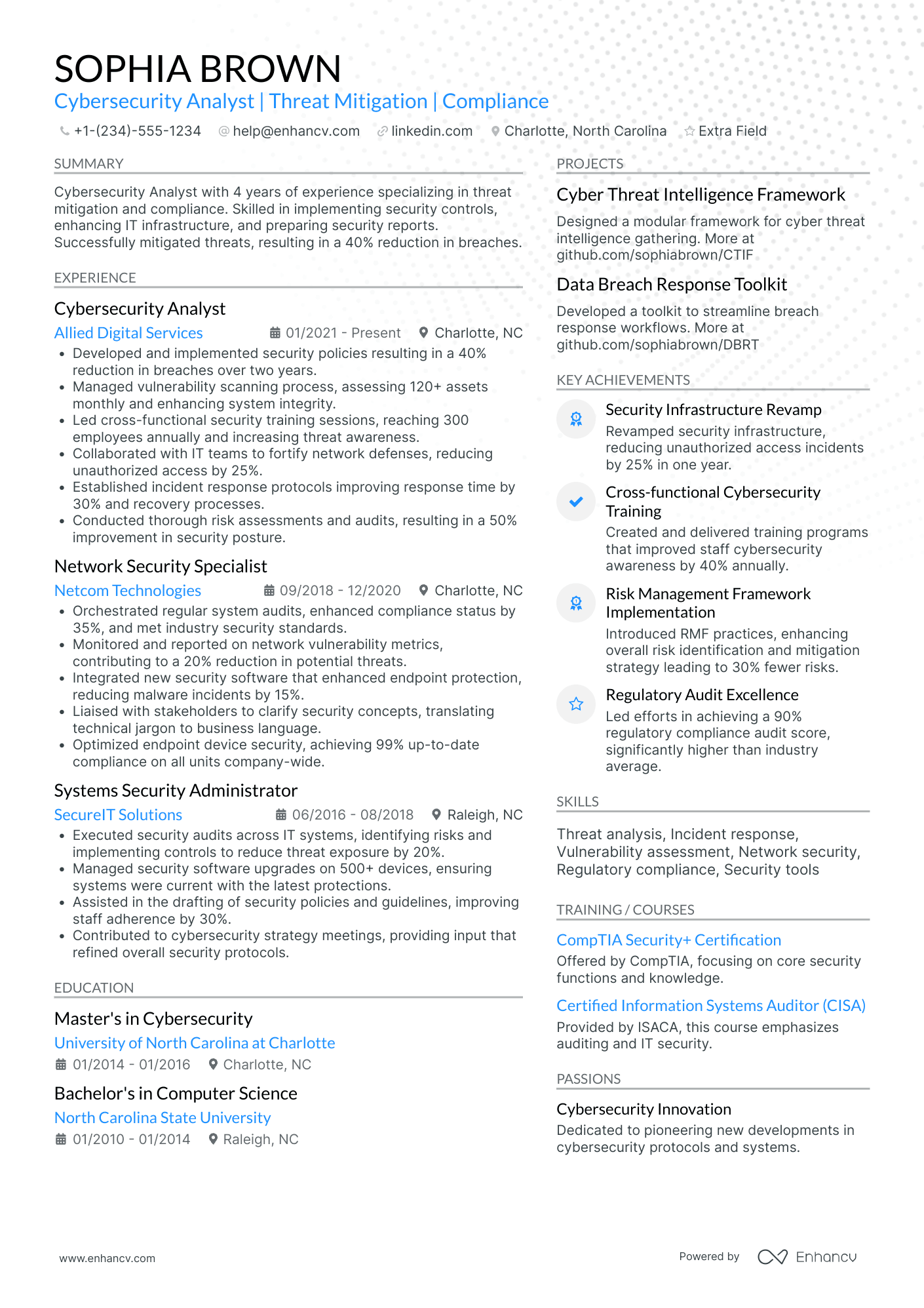
As a cybersecurity analyst, you’re an expert at identifying network weaknesses. But can you identify the weak spots in your resume?
According to a recent ISC2 cybersecurity workforce study, the global shortage of cybersecurity professionals has surpassed four million, yet competition for top roles remains fierce.
In this guide, you’ll learn how to tweak your cybersecurity analyst resume to withstand even the most rigorous screening and easily pass applicant tracking systems (ATS).
From front-line threat hunting to compliance oversight, let’s fortify your competencies and help you grab the attention of hiring managers in this competitive digital field.
Key takeaways
- Tailor your resume summary and experience with role-specific cybersecurity terms.
- Rename your skills section to “Technical Expertise” to convey competence.
- Align your technical abilities to the role and break down the section into relevant categories.
- Give examples of how your breach prevention methods resulted in cost-savings for businesses.
- Place your certifications before your education to prioritize your relevant know-how.
We’ll delve into every aspect of crafting a strong resume and provide plenty of inspiring examples. Let’s begin with the first one.
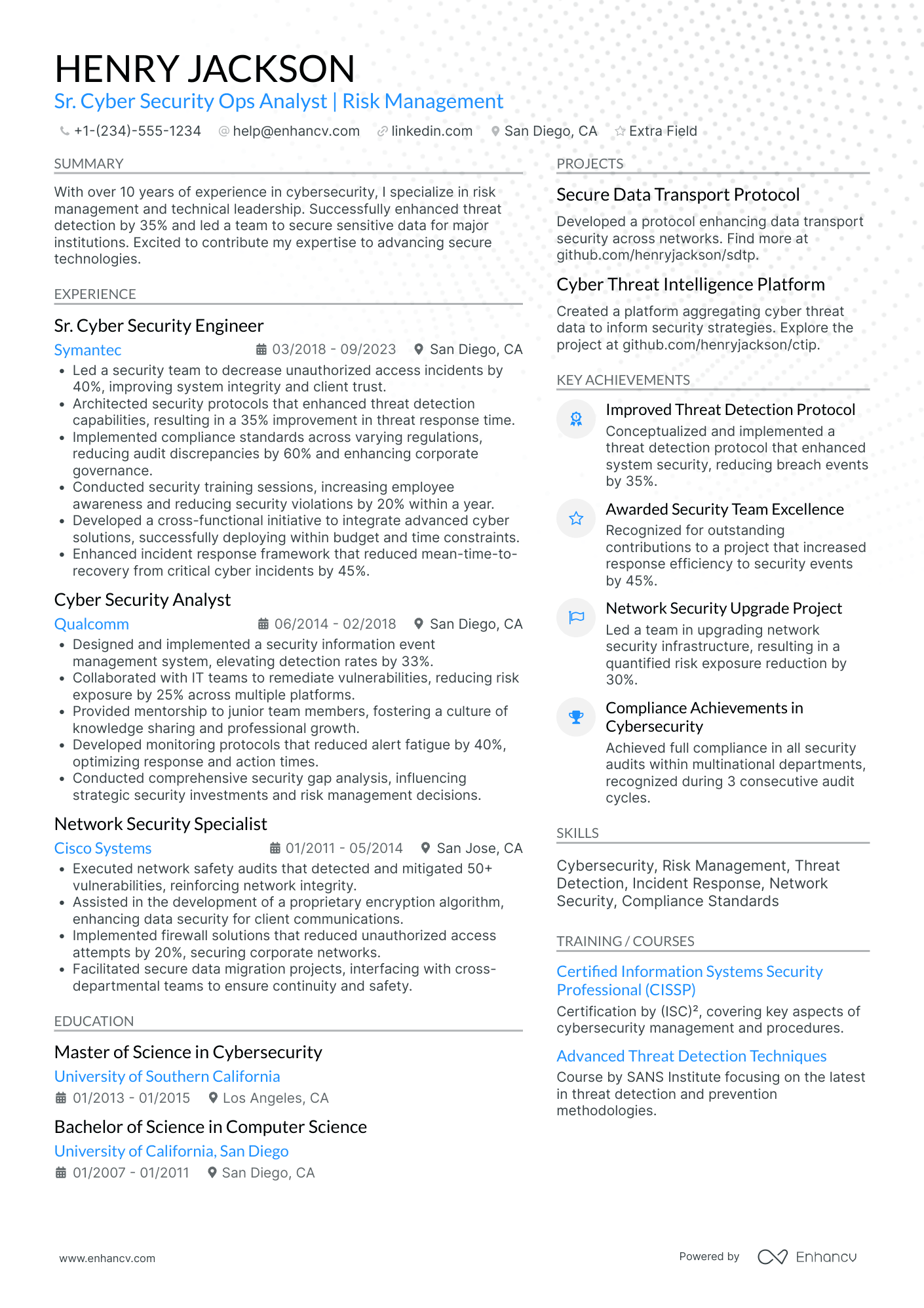
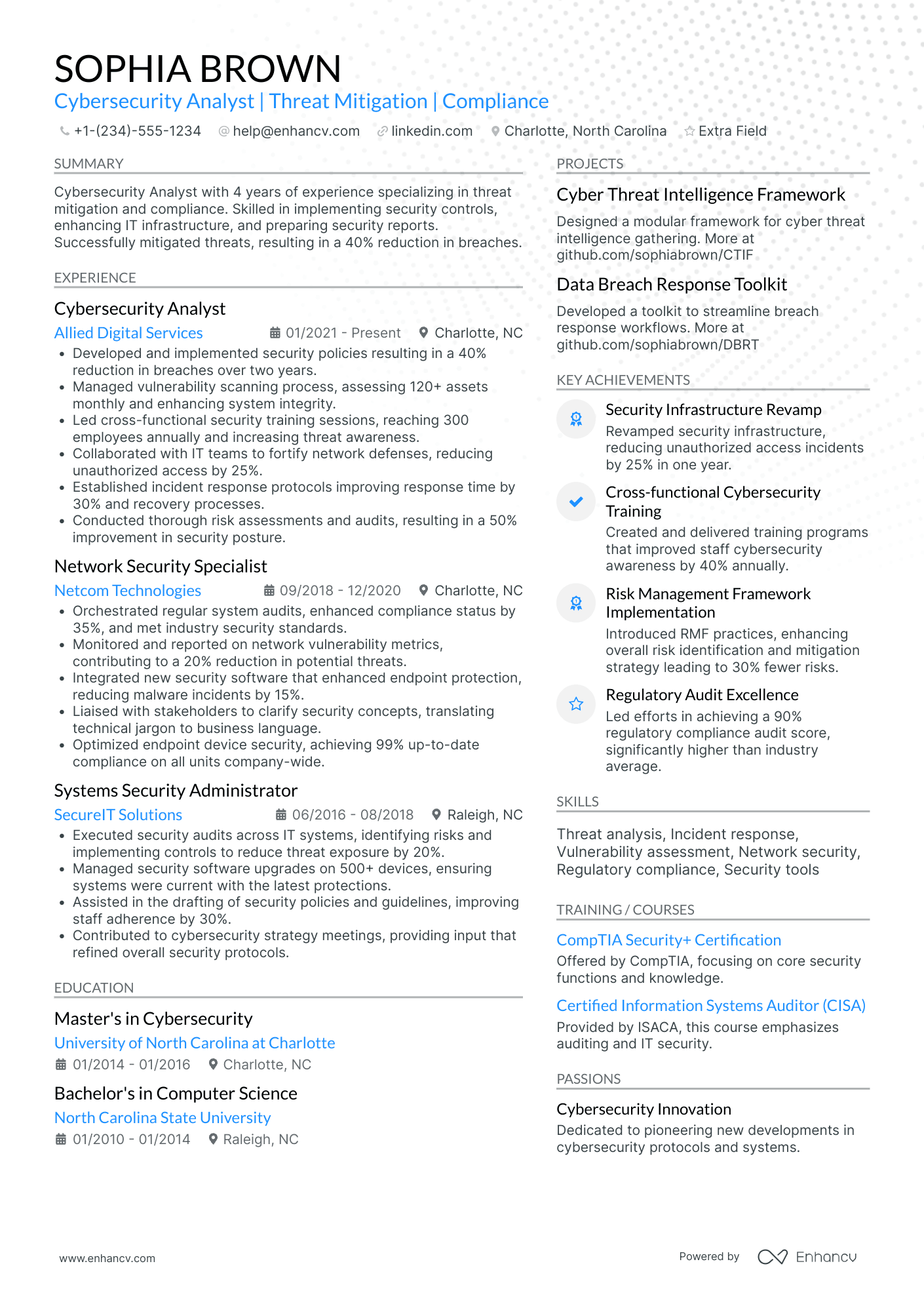
Cybersecurity analyst resume sample
Take a look at this cybersecurity analyst example resume. You can copy it and customize it in Enhancv’s AI-powered resume builder.
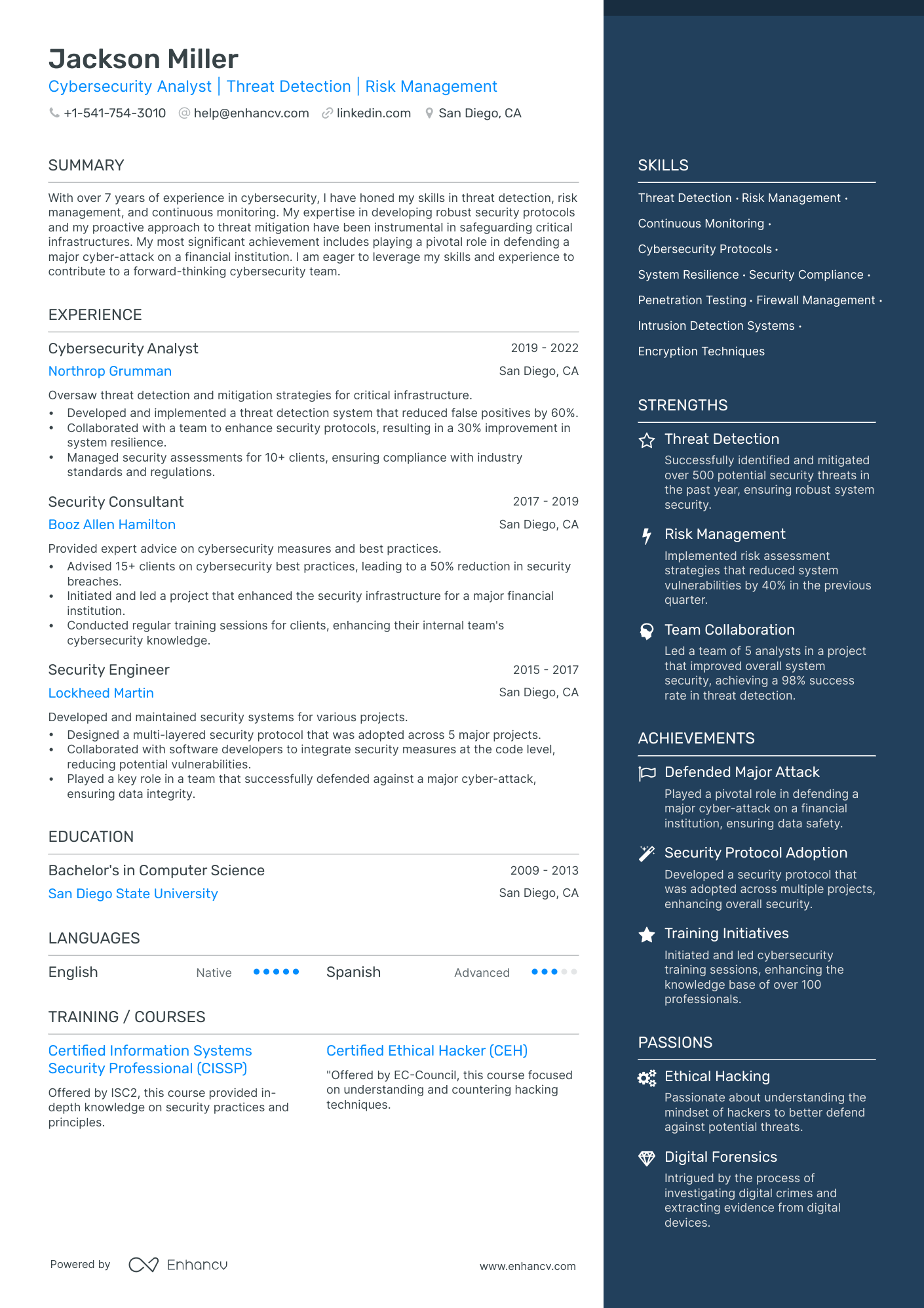
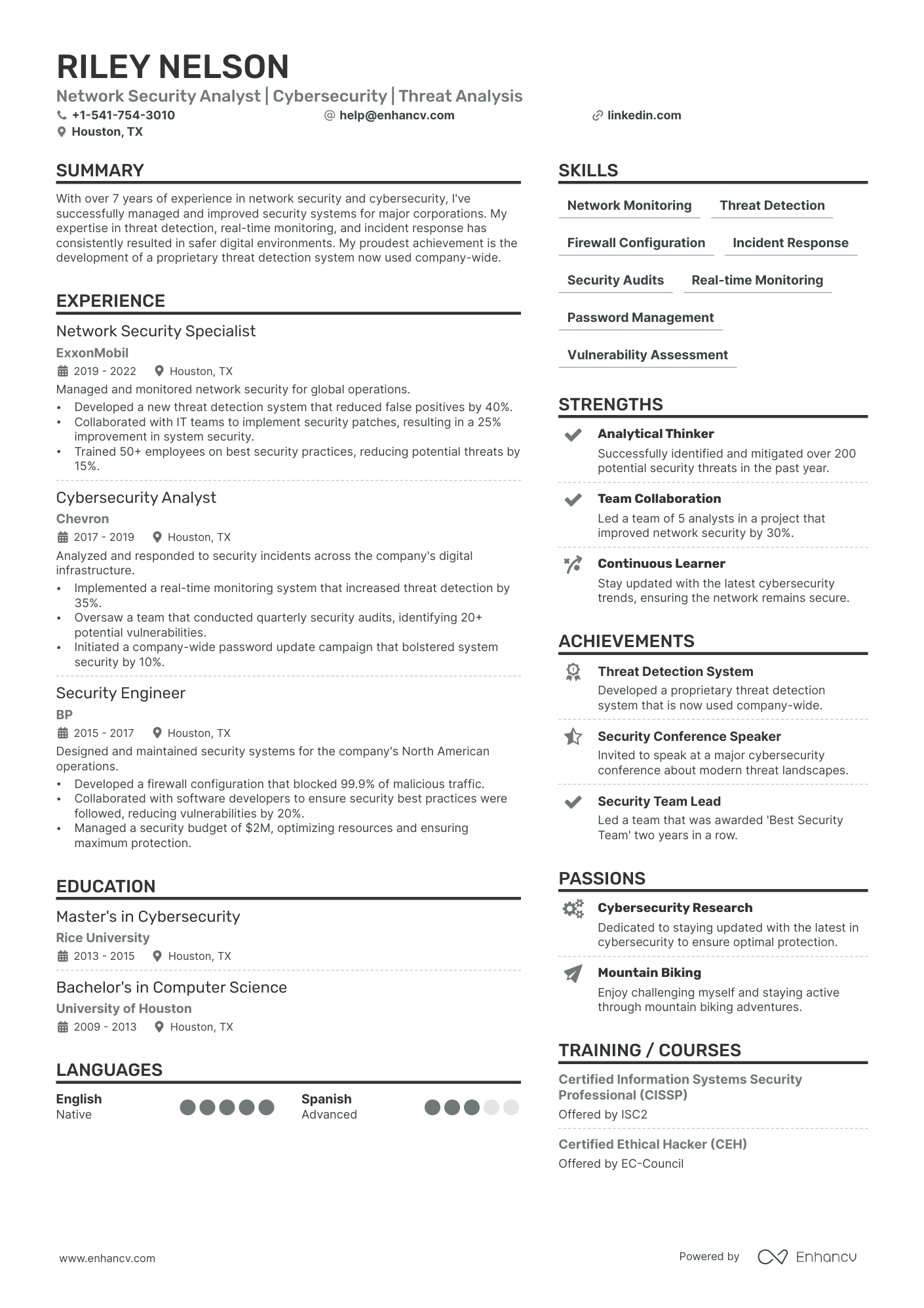
Adrian Thomas
Cybersecurity Analyst
(555)-173-87XX | adrian.thomas@enhancv.com | @LinkedIn | San Francisco, CA
Summary
Proactive and detail-oriented cybersecurity analyst with over four years of experience in threat detection, incident response, and vulnerability management. Skilled in deploying advanced SIEM tools and applying security frameworks like NIST and ISO 27001. Adept at collaborating with cross-functional teams to implement robust security controls and safeguard critical infrastructure. Looking to join ShieldSec Solutions to leverage cutting-edge methodologies and stay ahead of emerging cyber threats.
Technical Expertise
- Threat Analysis & Incident Response
- Vulnerability Assessments & Penetration Testing
- SIEM Tools (Splunk, QRadar)
- Security Frameworks (NIST, ISO 27001)
- Network Protocols & Firewall Administration
- Cloud Security (AWS, Azure)
- Collaboration & Communication
Professional Experience
Cybersecurity Analyst
DataShield Innovations, Seattle, WA
January 2021 – Present
- Perform comprehensive vulnerability assessments and penetration tests to identify high-risk threats
- Monitor real-time network activity using Splunk, isolating and containing suspicious behaviors
- Coordinate cross-functional incident response efforts, reducing recovery time by 40%
- Collaborate with compliance teams to integrate and maintain NIST security controls
- Provide mentorship to junior analysts on new threat vectors and best practices
Certification
- Certified Ethical Hacker (CEH) | 2024
- EC-Council
Education
Bachelor of Science in Cybersecurity
University of California | Berkeley, CA | Graduated: May 2021
- GPA: 3.8
- Relevant Coursework: Network Security, Ethical Hacking, Incident Response, Cryptography
- Capstone Project: Designed and implemented a secure network architecture for a simulated corporate environment.
Projects & Research
- Cloud Threat Monitoring Pilot – Deployed automated scripts to detect anomalous behavior in AWS-based systems, reducing false positives by 30%.
- Web Application Firewall (WAF) Optimization – Collaborated with DevOps team to optimize WAF rules, improving performance for a major e-commerce client.
This is just a text-only example. There’s a lot more you can do when it comes to formatting.
How to format a cybersecurity analyst resume
Formatting your cyber threat analyst resume can be the difference between getting a call from a hiring manager and being passed over.
A clear, strategic structure is necessary to present your expertise in the best possible light.
Best resume format for a cybersecurity analyst
A hybrid resume format is the best option for a cyber vulnerability analyst because hiring managers often want to see your relevant experience and skills immediately.
Resume design tips
In 2026, going for a one-page resume with a two-column layout is the perfect way to present your experience and technical skills. This will make your resume visually appealing and easy to scan.
However, if you have an extensive career in the field of cybersecurity—say, 10 years or so—then you can confidently present a two-page resume.
Here’s what else we recommend:
- Keep resume margins between 0.5"–1" to ensure your content is readable and printer-friendly.
- Use a neutral color scheme (e.g., black and subtle accent hues) to maintain a professional look.
- Opt for clean, classic resume fonts (like Calibri or Arial) in 10–12 pt size to ensure readability.
- Avoid excessive graphics because they can de-emphasize your experience and technical skills.
- Give Enhancv’s professional resume templates a try to save time.
Don’t worry about using modern resume templates. Current applicant tracking systems can parse them just fine.
Contact information
- Put your name, phone number, professional e-mail address, LinkedIn profile, and city/state in your header.
- You can also add links to your portfolio or GitHub.
- There’s no need to include a photo (avoiding negative bias), your age, or a complete mailing address.
File format and naming
It’s best to save your resume in PDF format.
Here’s why:
- ATS can easily extract text from it for keyword matching.
- Hiring managers expect it.
- It preserves resume formatting across devices.
Also, name the file appropriately, for example: name_surname_cybersecurity_analyst_resume.pdf
Top sections for a cybersecurity analyst resume
Here's how to organize your resume for maximum clarity and impact:
- Header with contact information
- Professional Summary
- Technical Expertise
- Professional Experience
- Certification & Education
- Projects & Research
We’ll discuss the rest of these resume sections in detail. But first, why don’t you give our free ATS resume checker a try?
Is your resume good enough?
Drop your resume here or choose a file. PDF & DOCX only. Max 2MB file size.
Now that we covered the basics of a good-looking IT security analyst resume, let’s get into what and how to write in each section.
How to write your cybersecurity analyst resume experience
Writing your experience section is one of the most important steps in creating a compelling cyber vulnerability analyst resume.
This is where you demonstrate your hands-on expertise in threat mitigation and incident response.
Here’s how you should approach it:
- Each work experience entry should include a role, company name and location, and employment period.
- Start with your most recent role and follow the reverse-chronology logic.
- Instead of listing responsibilities, impress hiring managers with real examples of how you prevented or mitigated cybersecurity threats.
- Use action verbs and numbers to draw attention to your accomplishments and make them tangible.
You can make your experience section even stronger by tailoring it to the job description.
Why resume tailoring is important
Think about this step of the resume writing process as somewhat “hacking” the job application system. It boosts your chances of getting a call for an interview.
Here’s why:
- Enriches your resume with keywords from the job description.
- Increases your chances of passing the ATS screening.
- Hiring managers will notice your attention to detail.
For example, you can address company-specific needs such as experience with hybrid cloud environments, and incorporate role-related keywords such as “SIEM integration” or “SOC analyst.”
To better demonstrate this approach let’s look at a job description example and apply some resume tailoring afterward.
Cybersecurity Analyst
Company Profile
ShieldSec Solutions is a forward-thinking cybersecurity firm specializing in proactive threat intelligence, incident response, and data protection strategies. Trusted by global enterprises in finance, healthcare, and government, our team applies cutting-edge security methodologies to safeguard critical systems and sensitive data. We believe in cultivating a culture of innovation, continuous learning, and collaboration to stay ahead of ever-evolving cyber threats.
Main Role Responsibilities
- Perform in-depth vulnerability assessments and penetration tests to identify potential risks.
- Monitor networks, systems, and applications for suspicious activity and promptly address threats.
- Coordinate incident response efforts, including containment, eradication, and recovery measures.
- Work closely with cross-functional teams implement security controls and compliance standards.
- Develop and maintain cybersecurity documentation, including incident reports and standard operating procedures.
- Provide mentorship and training to junior staff on security best practices and emerging technologies.
Requirements
- Bachelor’s degree in Cybersecurity, Computer Science, or a related field.
- 3+ years of hands-on experience in threat analysis, incident handling, or security operations.
- Proven expertise in security frameworks and standards (e.g., NIST, ISO 27001).
- Solid understanding of network protocols, firewalls, and SIEM tools.
- Industry certifications such as CompTIA Security+, CEH, or CISSP are strongly preferred.
- Excellent communication skills and the ability to thrive in a fast-paced environment.
As you’ve noticed, we’ve highlighted the parts of the job description that we’ll target in our experience section example below.
- •Performed in-depth vulnerability assessments and penetration tests to proactively identify high-risk threats
- •Monitored real-time network activity and system logs, swiftly containing suspicious behaviors
- •Coordinated cross-functional incident response efforts, ensuring seamless eradication and recovery
- •Collaborated with IT and compliance teams to implement security controls and meet industry frameworks (NIST, ISO 27001)
- •Provided mentorship and training to junior staff on latest security methodologies and best practices
We used the outlined responsibilities from the job description to form our action verbs and accomplishments, effectively turning the entry into a perfect match.
However, such an entry could be improved even further through the use of numbers and metrics.
How to quantify your experience on a resume
Quantifying your cybersecurity experience with concrete numbers and measurable results sets you apart from candidates who lack specificity. You can be certain that you’ll leave a lasting impression.
Here are a few recommendations:
- Include incident response metrics, such as reduced mean time to detect (MTTD) or mean time to respond (MTTR).
- Mention the specific types of threats you dealt with such as DDoS attacks or ransomware.
- List any specialized tools and frameworks you implemented.
- Describe cross-functional collaborations with various teams and departments.
- Put examples of proactivity and leadership, such as spearheading security awareness training or leading an incident response task force.
Here are some examples of what to include in your experience bullet points:
- Reduced incident response times by 45% through the implementation of automated threat detection workflows.
- Conducted over 250 vulnerability assessments annually, identifying and mitigating high-risk threats across critical systems.
- Increased phishing email detection rate by 60% by refining email filtering rules and deploying advanced AI-based tools.
- Secured $2 million in potential cost savings by preventing data breaches through enhanced endpoint protection measures.
- Improved network uptime by 30% by proactively addressing system vulnerabilities and optimizing firewall configurations.
Having such notable accomplishments in cyber threat analysis makes you a prime candidate for the role. But what if you lack experience?
How do I write a cybersecurity analyst resume with no experience
Writing a resume without direct experience for the cybersecurity analyst role is challenging. However, with the right approach, you can outshine even some experienced candidates.
For example, if you’re a recent graduate, opt for a functional resume format. Include details about your academic projects, certifications, and any cybersecurity competitions you’ve taken part in.
However, if you’re an IT professional with transferable skills, using a hybrid resume is the best way to present your competence. Focus on your relevant experience and technical skills and how you can apply them in cybersecurity.
A functional resume emphasizes education and skills, while a hybrid (or combination) resume blends elements of both reverse chronological and functional formats.
Here’s what else you should do:
- Stick to a one-page resume to concisely present your relevant competencies.
- Use industry- and job-specific terms to pass ATS screening.
- Demonstrate continuous learning by mentioning participation in cybersecurity communities and training platforms (e.g., TryHackMe, Hack The Box).
- Share your strong motivation to leverage your skills and knowledge in this role.
When it comes to motivation, the best place to express yours is in a resume objective.
Objective statement writing tips
A resume without direct cybersecurity experience should start with an objective rather than a summary.
Here’s how to write yours:
- Tailor the objective to the role and company.
- Mention certifications and transferable skills.
- Align your career goal with the hiring company’s priorities.
- Articulate your enthusiasm for the role.
- Be direct and concise in two to three sentences.
Here’s an example to inspire you:
However, if you’re aiming to land a senior role in network security, then you’ll find the next section particularly helpful.
Optimize your resume summary and objective for ATS
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
How to show career progression on a cybersecurity analyst resume
If you wish to advance in your cybersecurity career, your resume should reflect your professional growth.
Hiring managers are impressed by candidates who bring more than just technical skills to the table—they’re looking for individuals who can lead initiatives and solve complex problems.
The best way to position yourself as a candidate ready to step into a leading cybersecurity role is by demonstrating career progression on your resume.
Below are some effective ways to underscore your readiness to make an impact:
- Use the job description in the experience section to suggest an upward career trajectory by describing promotions and expanded responsibilities.
- Cite instances when you stepped into leadership positions, such as taking charge of incident response or guiding a team through containment.
- Mention collaborative efforts such as working with IT, compliance teams, or DevOps to improve security.
- List significant projects you owned such as leading security audits or designing new firewall architectures.
- Explain how you addressed advanced challenges like the implementation of zero-trust models or zero-day threats.
In the end, it all comes down to having the right set of skills and qualities for the job.
How to list your hard and soft skills on your resume
Information security is a quickly evolving sector, and it can be challenging to keep your skills list up to date. You need to be meticulous because listing outdated tools can expose you as someone who doesn’t stay current.
This is why, for applications in 2026, we recommend having a dedicated, carefully structured hard skills section.
Hard skills and soft skills are terms from resume-writing lingo. “Hard” refers to measurable, technical abilities while “soft” means interpersonal and behavioral traits.
Here’s what else we recommend:
- Change the section’s heading to “Technical Expertise” or “Tools & Technologies” to align your resume with the specific language of the field.
- Organize your technical skills into categories (e.g., "Network Security," "Cloud Security") to boost your competence and enrich your resume with relevant keywords.
- Prioritize the tools mentioned in the job description to tailor your resume.
- List skills in compliance standards if relevant to the role.
Here’s what technologies hiring managers expect to see in your skills section during 2026:
Best hard skills for your cybersecurity analyst resume
- Splunk
- Wireshark
- Nessus
- Qualys
- Metasploit
- Burp Suite
- Palo Alto Networks
- Cisco ASA
- Microsoft Defender ATP
- AWS Security Hub
- Azure Sentinel
- CrowdStrike Falcon
- Fortinet
- QRadar
- Kali Linux
- OpenVAS
- ZAP Proxy
- Snort
- OSSEC
- Darktrace
We don’t recommend having a separate section for your soft skills because it can detract from your technical expertise.
It’s best to mention some of them in other sections of your resume, such as your summary or work experience.
However, this doesn’t mean your personal qualities won’t be appreciated by hiring managers, especially if you can tie them to how you solved specific problems in the past.
Here are the traits you can connect to your technical know-how:
Best soft skills for your cybersecurity analyst resume
- Analytical thinking
- Problem-solving
- Communication
- Attention to detail
- Team collaboration
- Time management
- Adaptability
- Decision-making
- Risk assessment
- Conflict resolution
- Creativity
- Organizational skills
- Multitasking
- Active listening
- Strategic planning
- Emotional intelligence
- Leadership potential
When it comes to skills, it’s always better to back them up with credentials. This brings us to the next section of this guide.
How to list your certifications and education on your resume
The certifications section generally takes priority over education on a cybersecurity analyst resume.
They signal to hiring managers that you possess up-to-date, job-specific knowledge and skills—qualities often valued more than a formal degree.
To list your certificates, simply include their name, the year you obtained each, and the issuer.
Here are some of the certificates that hiring managers look for on threat intelligence analyst resumes in 2026:
Best certifications for your cybersecurity analyst resume
Still, listing your education, especially if you’ve graduated in a relevant field, should be done properly.
Here’s what to include in your education section:
- Degree title
- Institution name
- Location (optional)
- GPA score (optional, if above 3.5)
- Year of graduation (or "Ongoing" if not completed)
Here’s an example:
Now let’s move on to the section where it all comes together—your resume profile
How to write your cybersecurity analyst resume summary
Writing a summary might seem straightforward but there are a few best practices to keep in mind.
Though typically just three to four sentences long, its importance far outweighs its length.
Here’s how to write an impactful summary:
- Tailor the section to the job description and the hiring company.
- Mention how many years of direct cybersecurity experience you have.
- Strike a balance between technical expertise and soft skills.
- Include one of the key certifications relevant to the role.
- List one of your most significant measurable accomplishments.
- Use confident language but don’t exaggerate.
Here’s an example:
This summary establishes credibility quickly, balances technical expertise with interpersonal skills, and exudes confidence without seeming boastful.
In addition, you can mention a specific industry you’ve worked in (e.g., healthcare, finance, etc.) if you’re applying for a company in the same sector. Having niche experience will highly increase your suitability for the role.
Any hiring manager reading your summary will undoubtedly be impressed. Speaking of impressions, is there anything else you could add to your resume to make it even stronger?
Additional sections for a cybersecurity analyst resume
In some cases, your resume could benefit from additional sections, helping you to become a prime candidate for the role.
Here are some examples:
- Projects: Useful to demonstrate transferable experience or in-depth knowledge in cybersecurity areas that align with the role.
- Languages: Applicable for global companies or roles requiring diverse communication.
- Publications: Sets you apart as a highly dedicated contributor to the cybersecurity field.
- Awards: Having won cybersecurity competitions and hackathons is a testament to your technical proficiency and quick mind.
- Freelance Work: Validates your hands-on experience and technical skills gained outside of traditional employment.
In conclusion
Crafting an impressive resume in 2026 for a cybersecurity analyst role is all about presenting your core competencies in a structured and purposeful manner. You’ll significantly increase your chances of getting calls from hiring managers if you stick to the best practices outlined above.
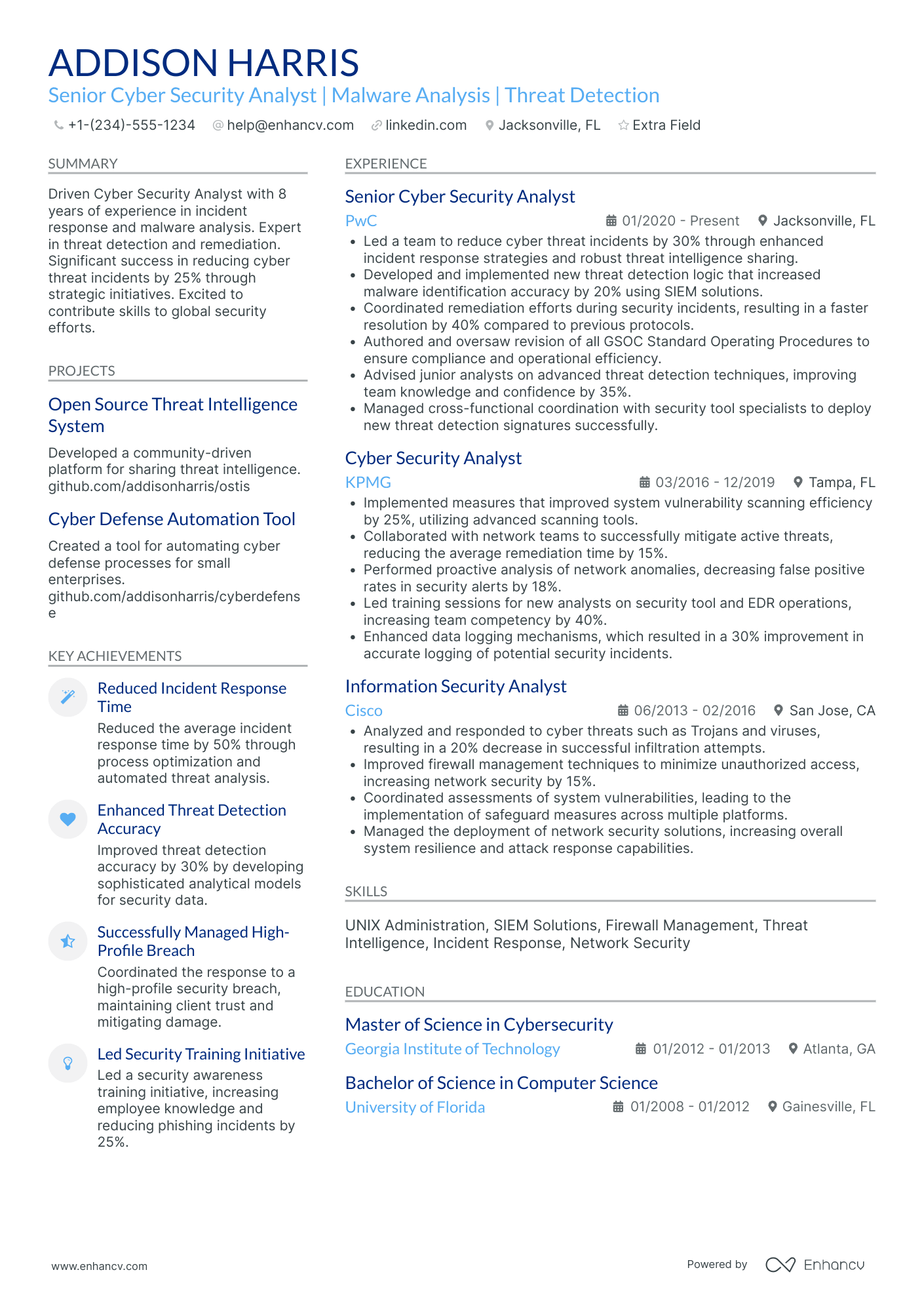
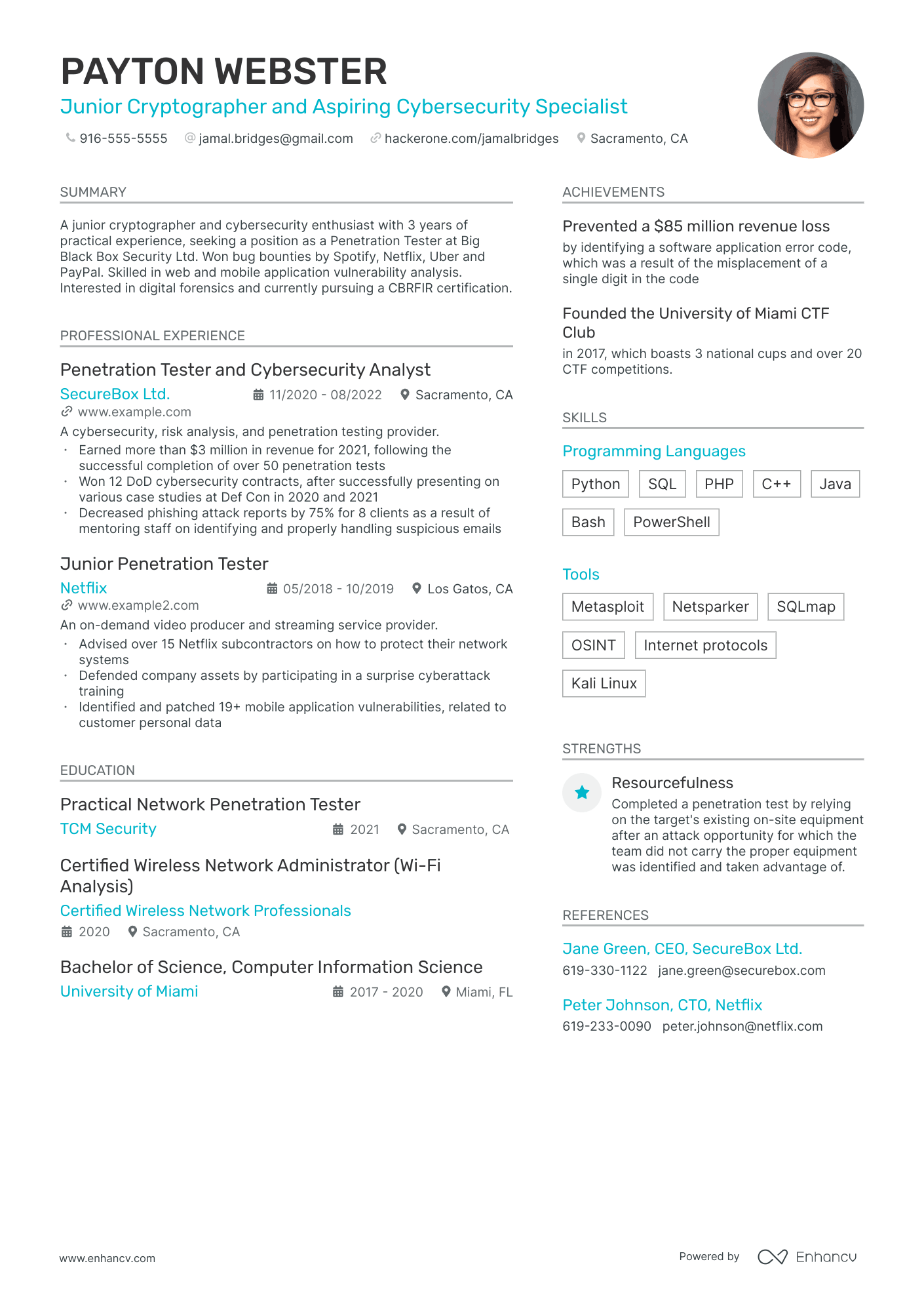
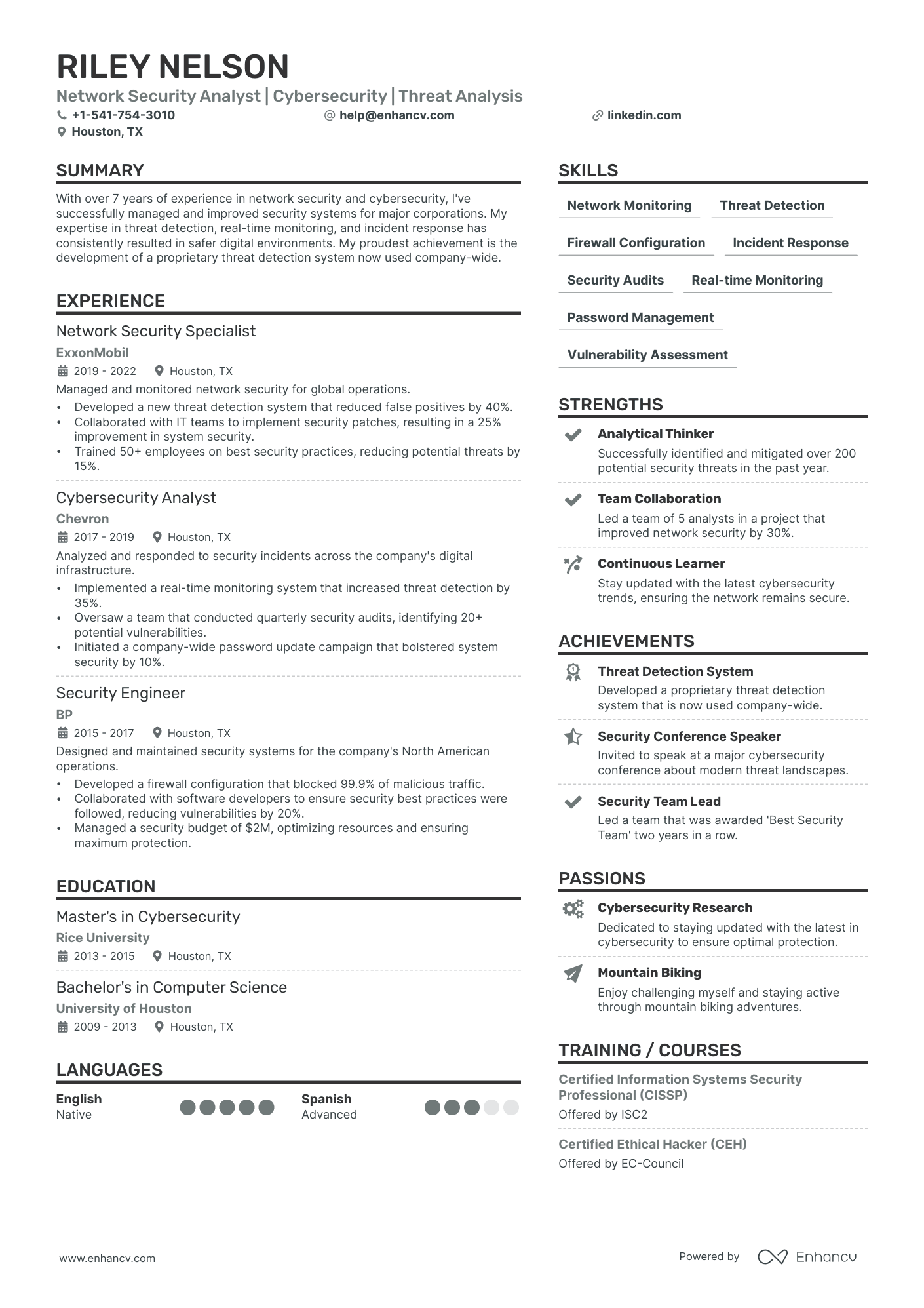
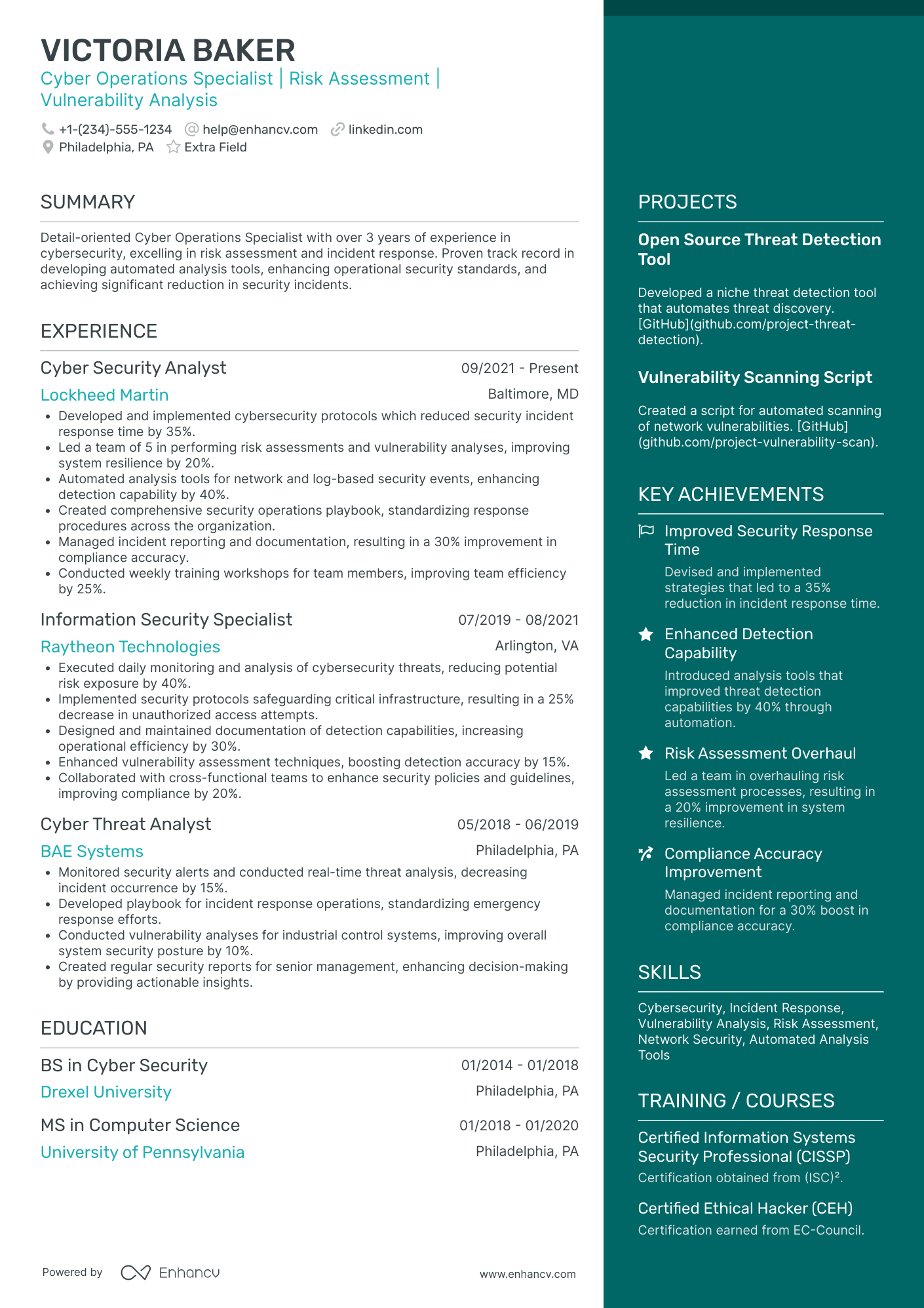
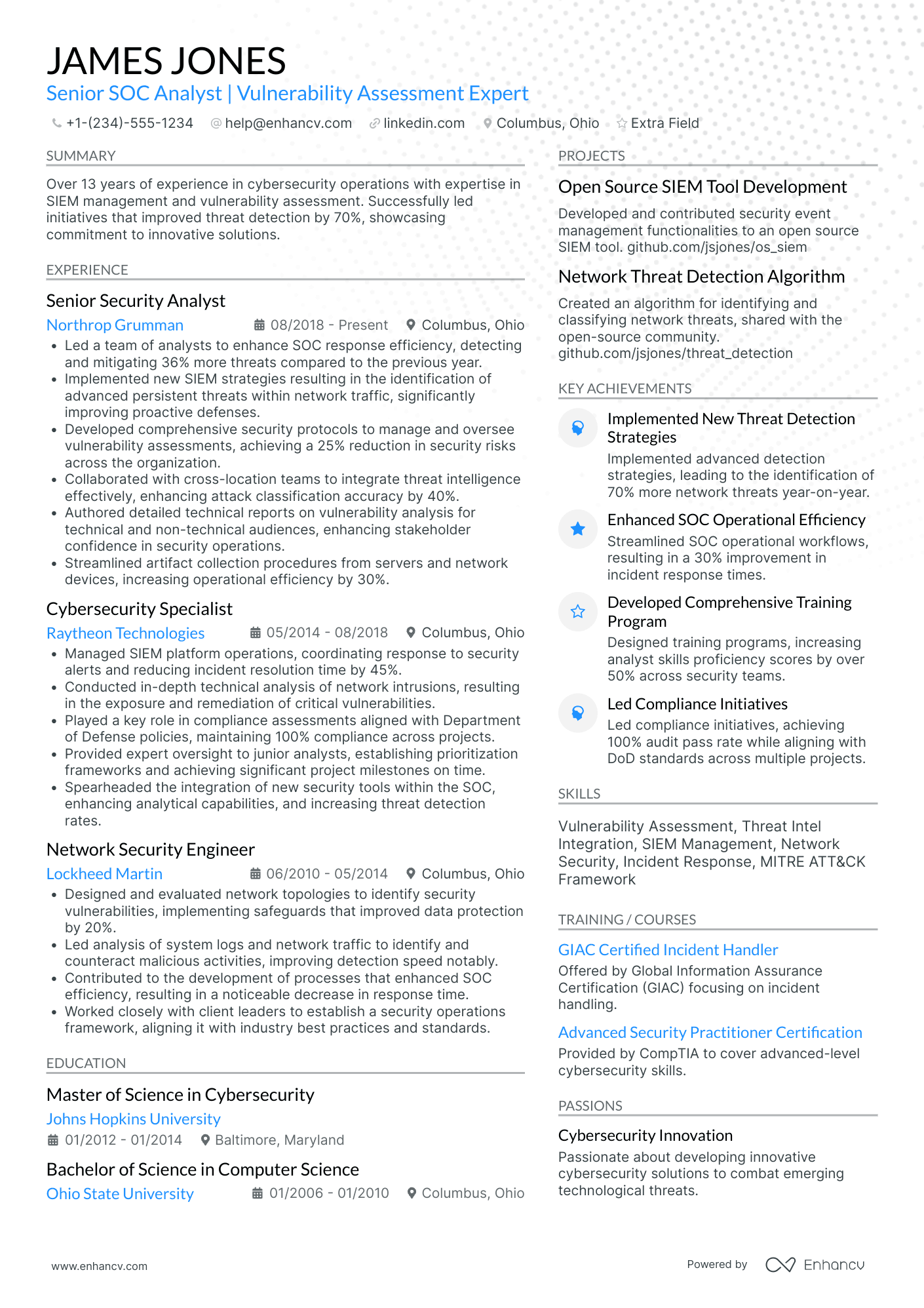
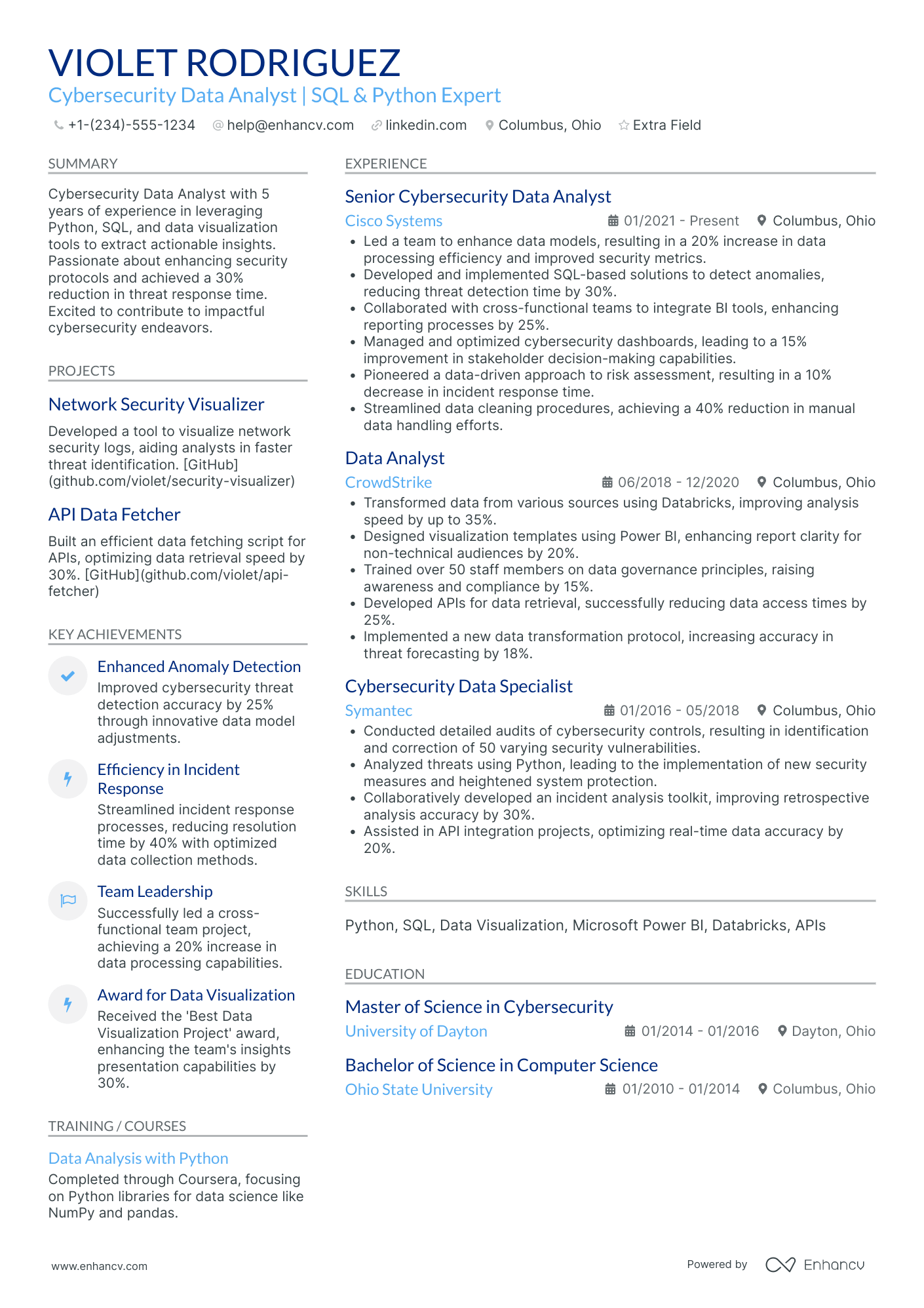
Cyber Security Analyst resume examples
By Experience
By Role